Syscom Intelligent Information Security Integration Service Platform
- Integrate traditional SOC (SIEM) and new generation SOC product functions.
- Establish information security status awareness (dashboard) and information security threat warning lights.
- With intelligent ISO management tools, we assist customers in establishing information security PDCA standard operating procedures.
- Satisfy customers operation needs via three major mechanisms: ISAC, SOC, and CERT.
- Assist large clients in building intelligence-driven cross-organization response and joint defense systems.
- Across the IT/OT/IOT field, tailor the most suitable security mechanism for customers.
Six characteristics
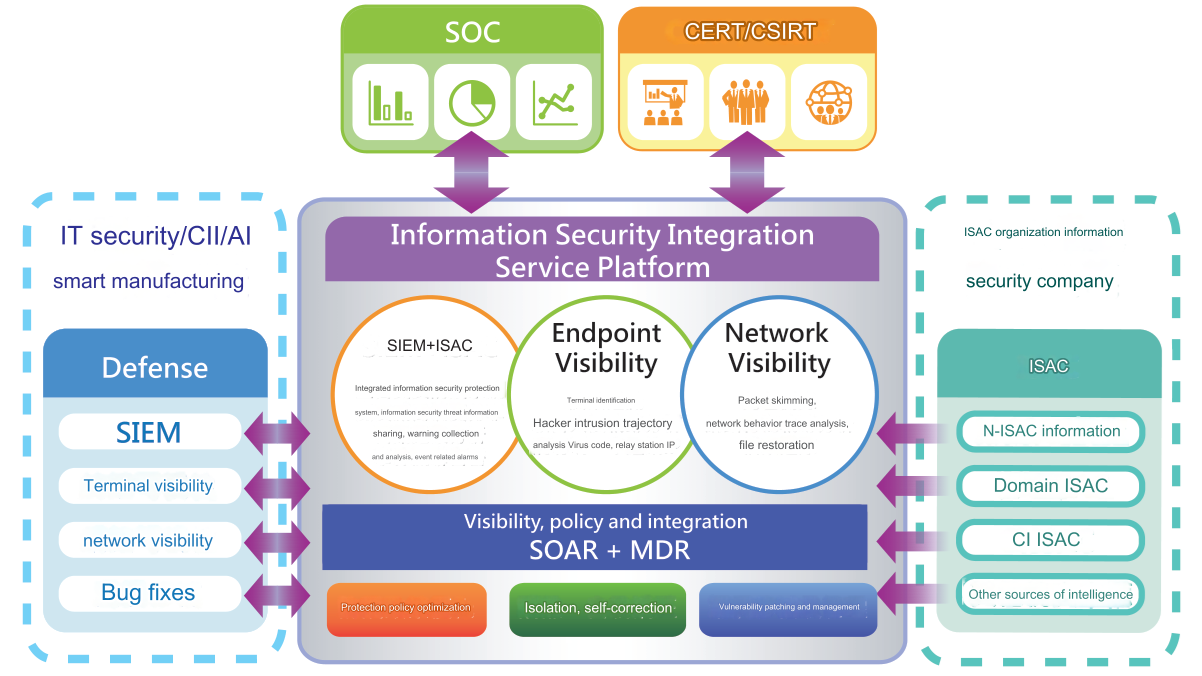
Syscom intelligent information security integration service platform Diamond Guard is a new generation of information security integration service platform that is different from traditional information security monitoring services (SOC). Its advanced tools and automated process engine carry out automatic serial checking of information security (early warning) information, the prevention of malicious behavior and the notification and processing of information security incidents (accidents), meeting the needs of enterprise information security information sharing (ISAC) and information security service monitoring (SOC) and Emergency Response Reporting (CERT) by following six characteristics.
1
Integrate traditional SOC (SIEM) and new generation SOC product functions
Different from the traditional SOC approach. It integrates terminal and network visibility tools and uses artificial intelligence, machine learning, big data analysis and other technologies to provide enterprises with comprehensive information security professional services for prevention pre-event, mid-event detection, and post-event response.
2
Establish information security status awareness (dashboard) and information security threat warning lights
With information security indicators that reflect actual conditions, it assists the chief security officer and information director to quickly identify the information security status and status of the enterprise itself.
3
Using intelligent ISO management tools to assist customers in establishing information security PDCA standard operating procedures
Through the automated process engine, standard SOPs for various information security tasks are established, so that knowledge can be continuously refined, accumulated and passed on.
4
Satisfy the operation needs of the three major operating mechanisms of customers ISAC, SOC, and CERT
Combined with the automated process engine, it connects ISAC pre-prevention, SOC event detection, and CERT event response operations in series, so that each link is comprehensively executed and completed.
5
Assisting large customers to build an intelligence-driven cross-organization response defense system
With a hierarchical system operation structure, it integrates information sharing, transmission, and automatic serial checking functions to assist enterprises in building a cross-organization reporting and response joint defense system, and exert the effect of comprehensive defense against single-point hacking!
6
Across the IT/OT/IOT field, tailor the most suitable security mechanism for customers
Integrating the industry’s top information security monitoring tools, SIEM platform and self-developed automated process engine, across the IT/OT/IOT field, tailor-made a comprehensive and optimal information security monitoring and reporting emergency handling mechanism for customers.
Three core functions
The overall platform primarily includes three core function modules: “system main module”, “network visibility module” and “terminal visibility module”
It includes five modules including service platform portal, service platform system management, intelligence application processing, joint protection, and operation process management.
Provide a digital dashboard for instantly displaying information security status and threat warning lights.
Provides to-do list control function and displays execution progress and completion time limit of the to-do list according to the role of the logged-in user (information security manager/network manager/host system manager/website manager).
Provides system parameter settings and hierarchical subordinate management functions, which can be set according to the operating environment and subordinate agency structure.
Provides information application processing functions, integrates government information security information analysis and sharing platform (NISAC), automatically receive various information sources from NISAC/field ISAC/other (in conformity with STIX format) and other information sources through system settings, and quickly determine the latest early warning information.
Provides an automated process engine and a built-in information security operation standard process to automatically search for information like security information ANA/information security warning EWA/web page attack DEF/intrusion attack INT/feedback FBI including terminal identification, network packet access, malicious file analysis, and more. After confirmation by SOC professional analysts, automatic joint protection including IP anti-blocking of malicious relay stations, virus code delivery, and more.
Provides traditional SOC (SIEM) integration functions, integrates the internal alarm information generated by the SIEM platform into the information application processing module management, and perform automatic serial inspection and joint protection.
Provide CERT integration function, through the automated process engine, for events that are automatically checked and confirmed by internal and external intelligence, implement control operations such as impact level analysis, website notification, damage control, recovery operations, and remedial improvement measures.
Provide incident response processing database function, which can accumulate experience in incident response processing, and provide online auxiliary functions such as damage control, recovery operations, and remedial improvement measures.
Network traffic monitoring and sensing system
It has the functions of real-time recording, storage, retrieval, and information security analysis of original packets of network traffic, and can be flexibly deployed on external Internet (Internet) gateway exits (Gateways) and internal important network access nodes, and provides central control (Central Console) functions.
Equipped with network traffic packet intermediary data (Metadata) analysis and extraction technology, supports a variety of network communication protocols, including network layer protocols (IP, ICMP), transport layer protocols (TCP, UDP) and application layer protocols (HTTP, TLS, DNS) , SMB, SSH, SMTP, MySQL, etc.).
It can save the intermediary data (Metadata) of each communication protocol and the original PCAP file of the traffic, and provide high-speed retrieval function. The search function must support Boolean logic conditional operations, and can freely combine network layer, transport layer, and application layer protocol intermediary data field values to form query conditions, and export corresponding PCAP format files based on the conditions.
The search function supports keyword search and regular expression (Regular Expression) filtering mechanism.
Users can define the characteristic values of abnormal connection behavior according to the protocol and network packet characteristics, and provide a marking mechanism and a search function for customized marked data to facilitate forensic analysis operations.
Provides a visual network identification function, which can draw a network attack connection topology map based on the search results, and clearly present key information and associations such as source and target IP connection addresses, connection ports, countries, and more.
Endpoint threat identification system analysis platform
Displays important system information such as the number of host endpoints scanned daily, distribution of suspicious program threat assessment levels, daily/weekly/monthly host endpoint scan overview (overview), ThreatSonar endpoint threat identification system server status, etc. Users can quickly grasp the daily malware scanning status through this function.
Host endpoints can be filtered based on different departments, malware threat levels, time, and other conditions. The screening results can display the host where the suspicious program is located, the host IP, the host Hostname, the operating system version, and the identity under which it is executed.
The original memory identification technology, equipped with heuristic rules, for analyzing the contents of the memory to determine whether there are hidden hacker threat tools or tracks and through horizontal communication between tracks, trigger behavior based on a complete outline of the endpoint device encountering hacker attacks. The infection chain and timeline enable managers to accurately identify the source and spread of possible hacker attacks, and formulate correct and effective plans for future security enhancement measures.
Functions for customed editing of Yara rule. Since each information security personnel has different information and experiences, this function assists information security personnel to enhance features and improve detection efficiency.
Provides threat hunting (Threat Hunting) function to help dig out Level 1 ~ 3 suspicious events (Outlier), and discover related threats, including: program, file path and name, hash value (hash), domain name, IP, and others. Filter by Interference factor, using statistical methods to find programs with abnormal characteristics (such as: outliers) in the deployment range, helps suppress cyber espionage attacks.
Endpoint threat detection system scanner
Uses the existing AD or asset management system dispatch mechanism to complete the automatic periodic threat hunting work schedule setting.
There is no need to install a resident program. It scans in the background and usually does not use hardware resources at the endpoint, particularly there are no drivers so this removed compatibility issues.
The Endpoint Threat Forensic Scanning Program scans the user’s host memory, files, network connections, system login files, machine codes, startup programs, executable programs, files, dynamic link libraries, and more, to find infected hosts.
The scanning program performs threat identification according to the specified schedule, and the scanning results are encrypted and sent back to the threat analysis platform. Next the threat analysis platform generates a threat analysis report. Information security personnel quickly identify the status of information security on the threat intrusion assessment platform at any time.
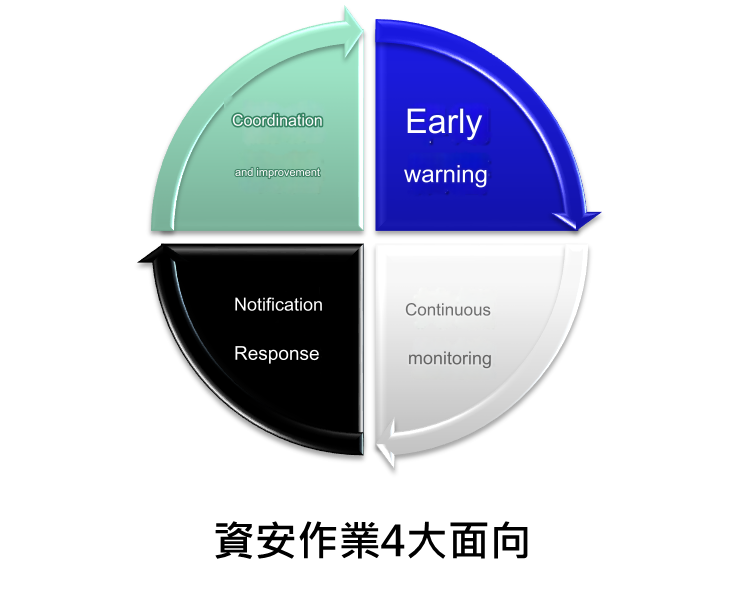
Four aspects
Syscom “Intelligent Information Security Integration Service Platform Diamond Guard” can satisfy government agencies and private enterprises to follow (cooperate with) government information security policies and integrate four aspects of information security operations: early warning (ISAC) and real-time monitoring (SOC) , CERT and other information security operation mechanisms.